If you’re reading this with a web3 plugin installed, it’s already too late. Your web3 client is telling us way more about you than you probably want us to know. Along with this post we deployed a small snippet of JavaScript that sends us information about your web3 accounts. If you’re here we know whether you’re using web3, and if your account is unlocked we know your Ethereum address. This post will talk about what information your browser is leaking to us and anyone else who wants it, and what you can do to protect yourself.
Traditional User Tracking
Tracking users is nothing new. Since the early days of the web, sites have been using cookies to track users across multiple page views. As users got smarter about blocking and deleting cookies, online trackers came up with other clever ways to fingerprint your browser and track you over time. Some examples of information that can help identify you across different websites even without cookies include:
- IP Address
- User Agent String, which tells your operating system and browser version
- Language Settings
- Screen Resolution
- Time Zone
- Installed Fonts
- Installed Browser Plugins
- Graphics Card Version
All of these things combine to create a pretty unique fingerprint that can help advertisers track your browsing habits from one site to the next.
Adding Web3
If you’re using a web3 plugin like Metamask it’s a lot worse.
Web3 is an interface that allows websites to interact with the Ethereum blockchain, the Swarm storage network, and the Whisper messaging protocol from the browser. Most people who use web3 use a browser plugin like Metamask that will inject a web3 object into every web page, allowing the website to interact with the blockchain on behalf of the user.
When you start your browser Metamask starts out locked, so until you manually unlock your account all we can see is that you have a web3 client running. From a traditional browser fingerprinting approach, this is one more piece of information to add to a long list of values that can make a user’s browser unique. A plugin that a tiny fraction of web users are using can turn a fairly common browser configuration into something completely unique.
Once you unlock your account we can get a lot more information. When you unlock Metamask, every tab you have open gets access to your Ethereum Address. This means they can determine your ETH balance, token balances, what contracts you’ve interacted with, what ENS domains you hold, whether you play Crypto Kitties, and the list goes on. Even if you’re unlocking Metamask to check your token balances on MyEtherWallet, every other tab you have open will get access to your Ethereum address. Metamask allows you to have multiple Ethereum accounts, and any time you switch accounts any tab you have open can observe the switch and track that both of those accounts belong to the same user.
What Can You Do About It?
Well, blog.openrelay.xyz is being transparent about the fact that we’re collecting your web3 information. You could avoid us in the future, but that does nothing to help protect you from all the other sites out there that are snooping your web3 object more discreetly.
Instead, you should try to separate your web3 activity from the rest of your browsing activity. Chrome and Chromium browsers make it really easy to create separate browser profiles. These profiles keep almost everything about your browsing experience separate. You get:
- Separate sets of cookies
- Separate browser plugins
- Separate local storage profiles
To create a separate profile in Chrome, click your profile name in the upper-right-hand corner of your browser:
This will show a list of available profiles.
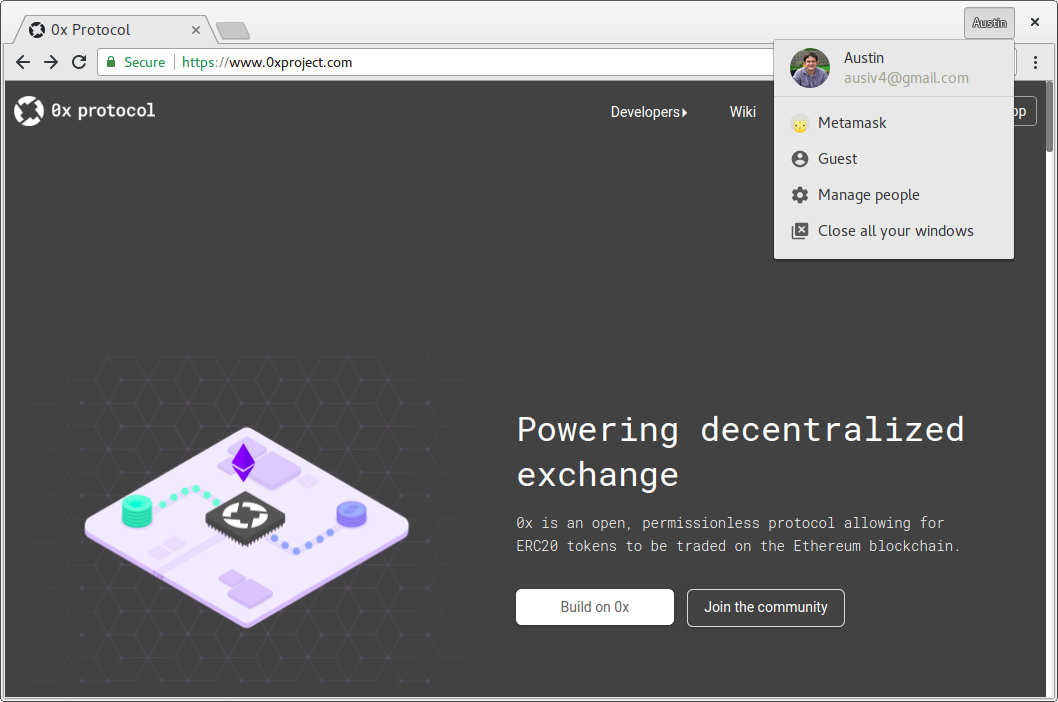
If you’ve already created a separate profile for Metamask, you can select it here to open a window for that profile. Otherwise click “manage people” to start creating a new profile.
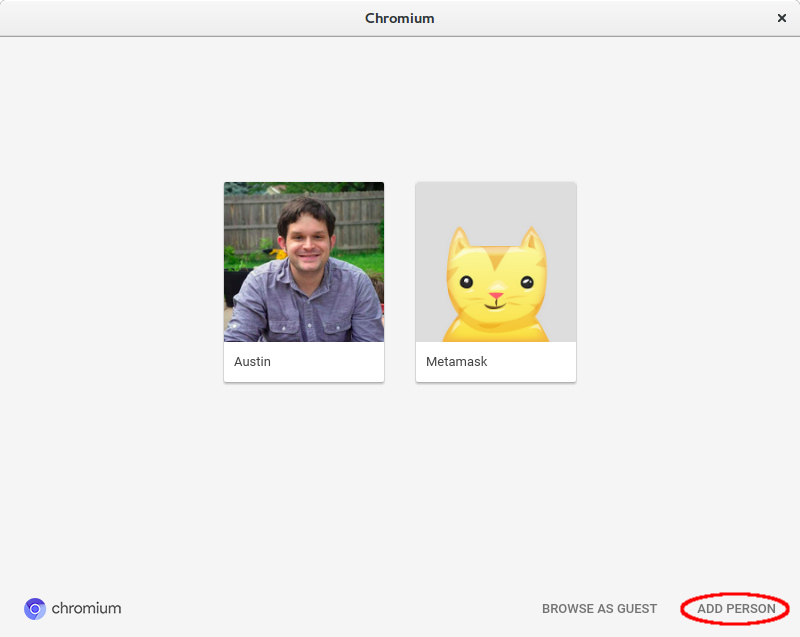
This will open a window with a list of existing profiles. In the lower-right corner of this window is an “Add Person” button. On the next screen just enter a name and pick an icon, then you’ll have a whole new browser profile.
In your new browser profile, install the Metamask plugin. Assuming you already use Metamask, you’ll probably want to configure Metamask in the new profile using the same seed words you used in your old profile.
Once you have Metamask configured, you can use your old profile and new profile side-by-side. You can browse the web on one, while only interacting with web3 related services on the other profile.
Once you’ve confirmed that your new profile is working, you should uninstall or disable the Metamask extension on your old profile to avoid leaking any extra information. Also be aware that if you have multiple tabs open on your Metamask profile, any of them can see when you unlock or switch between accounts.
What Else Could Be Done
Most of this post has focused on what end-users can do to protect themselves from snooping. There are steps that plugin makers like Metamask could take as well.
One option would be to have users whitelist which sites get a web3 injection. Until a user clicks on the metamask icon in their browser while looking at a particular tab, metamask could not inject the web3 object into the page.
Another option would be to avoid giving sites access to the web3.eth.getAccounts() method without user approval. Even if websites could see that a user had a web3 injection, it would prevent the sites from getting personal information without the user’s approval.
To be clear, I don’t want to knock Metamask. They’ve done some great things to make DApps more accessible to the public, and have done a very good job at keeping users assets secure in the process. The current implementation leaves a lot to be desired in terms of privacy, but there are solutions available.
What’s Next
In a few weeks I plan to follow up this blog post with some anonymized aggregate statistics about the web3 usage of the readers of blog.openrelay.xyz. I’m not going to release anything like specific addresses of visitors, but I do plan to release:
- Percentage of users with web3 injections
- Percentage of users with their accounts unlocked
- Total ETH held by users with unlocked accounts
- Highest ETH balance of any user with an unlocked account (rounded to protect anonymity)
- A list of popular tokens held by users with unlocked accounts
Until Metamask releases an update that breaks my data collection script, I’ll post periodic updates with those statistics. Hopefully we’ll see some of the numbers start to drop after this blog post.
Update
It took longer than I’d hoped, but we’ve finally published the stats from this experiment.
